三 实验一(route命令实现)
3.1小实验:网络拓扑图如下
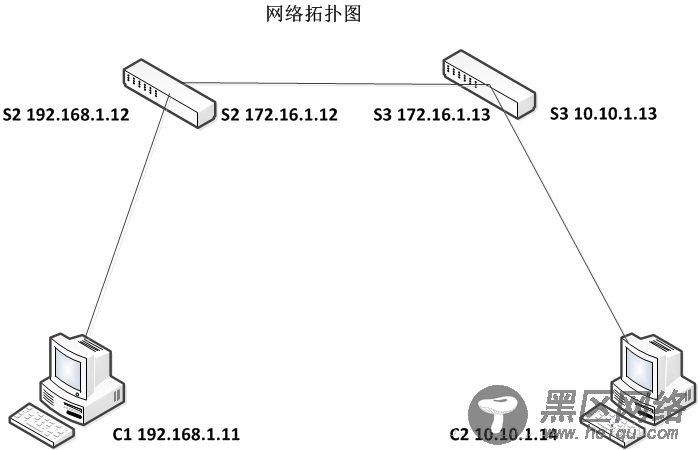
3.2目标
client01(192.168.1.11)可以ping通client2(10.10.1.14)
[root@client01 ~]# ping 10.10.1.14
connect: Network is unreachable
3.3 准备工作
3.3.1.关闭防火墙和SELINUX
[root@client01 ~]# service iptables stop
[root@client01 ~]# setenforce 0
3.3.2.虚拟机配置
Client01:使用Vmnet1
Serv02:使用Vmnet1、Vmnet2
Serv03:使用Vmnet2、Vmnet3
Client02:使用Vmnet3
3.3.3.配置IP,并测试相邻机器的IP地址是否能ping通
#第一台机器
[root@client01 ~]# ifconfig eth0192.168.1.11 netmask 255.255.255.0
[root@client01 ~]# ping 192.168.1.12
[root@client01 ~]# ping 192.168.1.1
#第二台机器
[root@serv02 ~]# ifconfig eth0 192.168.1.12netmask 255.255.255.0
[root@serv02 ~]# ifconfig eth1 172.16.1.12netmask 255.255.255.0
[root@serv02 ~]# ping 192.168.1.11
[root@serv02 ~]# ping 192.168.1.1
#第三台机器
[root@serv03 ~]# ifconfig eth0 172.16.1.13netmask 255.255.255.0
[root@serv03 ~]# ifconfig eth1 10.10.1.13netmask 255.255.255.0
[root@serv03 ~]# ping 172.16.1.12
[root@serv03 ~]# ping 172.16.1.1
#第四台机器
[root@client02 ~]# ifconfig eth0 10.10.1.14netmask 255.255.255.0
[root@client02 ~]# ping 10.10.1.14
[root@client02 ~]# ping 10.10.1.1
3.4.解决
#第一台机器
#添加默认网关
[root@client01 ~]# route add default gw192.168.1.12
#修改sysctl.conf文件,net.ipv4.ip_forward改为1,然后执行sysctl-p让修改生效
[root@serv02 ~]# vi /etc/sysctl.conf
[root@serv02 ~]# sysctl -p
[root@client01 ~]# sed "7p"/etc/sysctl.conf -n
net.ipv4.ip_forward = 1
#第二台机器
#添加路由,指定10.10.1.0网段的IP从172.16.1.13出去
[root@serv02 ~]# route add -net 10.10.1.0netmask 255.255.255.0 gw 172.16.1.13
#修改sysctl.conf文件,net.ipv4.ip_forward改为1,然后执行sysctl-p让修改生效
[root@serv02 ~]# vi /etc/sysctl.conf
[root@serv02 ~]# sysctl -p
[root@serv02 ~]# sed "7p"/etc/sysctl.conf -n
net.ipv4.ip_forward = 1
#第三台机器
#添加路由,指定192.168.1.0网段的IP从172.16.1.12出去
[root@serv03 /]# route add -net 192.168.1.0netmask 255.255.255.0 gw 172.16.1.12
#修改sysctl.conf文件,net.ipv4.ip_forward改为1,然后执行sysctl-p让修改生效
[root@serv02 ~]# vi /etc/sysctl.conf
[root@serv02 ~]# sysctl -p
[root@serv03 /]# sed "7p"/etc/sysctl.conf -n
net.ipv4.ip_forward = 1
#第四台机器
[root@client02 ~]# route add default gw10.10.1.13
#修改sysctl.conf文件,net.ipv4.ip_forward改为1,然后执行sysctl-p让修改生效
[root@serv02 ~]# vi /etc/sysctl.conf
[root@serv02 ~]# sysctl -p
[root@client02 ~]# sed "7p"/etc/sysctl.conf -n
net.ipv4.ip_forward = 1
3.5效果
#客户机1ping客户机2
[root@client01 ~]# ping 10.10.1.14
PING 10.10.1.14 (10.10.1.14) 56(84) bytesof data.
64 bytes from 10.10.1.14: icmp_seq=1 ttl=62time=1.84 ms
64 bytes from 10.10.1.14: icmp_seq=2 ttl=62time=0.856 ms
64 bytes from 10.10.1.14: icmp_seq=3 ttl=62time=1.13 ms
64 bytes from 10.10.1.14: icmp_seq=4 ttl=62time=0.805 ms
64 bytes from 10.10.1.14: icmp_seq=5 ttl=62time=0.866 ms
64 bytes from 10.10.1.14: icmp_seq=6 ttl=62time=0.730 ms
64 bytes from 10.10.1.14: icmp_seq=7 ttl=62time=0.596 ms
64 bytes from 10.10.1.14: icmp_seq=8 ttl=62time=0.788 ms
64 bytes from 10.10.1.14: icmp_seq=9 ttl=62time=0.741 m
#路由器1抓取来自客户机1的包
[root@serv02 ~]# tcpdump -i eth0 host192.168.1.11
tcpdump: verbose output suppressed, use -vor -vv for full protocol decode
listening on eth0, link-type EN10MB(Ethernet), capture size 65535 bytes
01:10:02.177598 IP 192.168.1.11 >10.10.1.14: ICMP echo request, id 26629, seq 65, length 64
01:10:02.178496 IP 10.10.1.14 >192.168.1.11: ICMP echo reply, id 26629, seq 65, length 64
01:10:02.179861 IP 192.168.1.1.51524 >192.168.1.11.ssh: Flags [.], ack 1140604063, win 472, options [nop,nop,TS val30797133 ecr 5038478], length 0
01:10:02.179882 IP 192.168.1.11.ssh > 192.168.1.1.51524:Flags [P.], seq 4294967201:1, ack 0, win 429, options [nop,nop,TS val 5038478ecr 30796131], length 96
#路由器2抓取来自客户机1的包
[root@serv03 /]# tcpdump -i eth0 host 192.168.1.11
tcpdump: verbose output suppressed, use -vor -vv for full protocol decode
listening on eth0, link-type EN10MB(Ethernet), capture size 65535 bytes
01:10:18.038232 IP 192.168.1.11 >10.10.1.14: ICMP echo request, id 26629, seq 81, length 64
01:10:18.038655 IP 10.10.1.14 >192.168.1.11: ICMP echo reply, id 26629, seq 81, length 64
01:10:19.039708 IP 192.168.1.11 >10.10.1.14: ICMP echo request, id 26629, seq 82, length 64
01:10:19.040050 IP 10.10.1.14 >192.168.1.11: ICMP echo reply, id 26629, seq 82, length 64
#客户机2抓取来自客户机1的包
[root@client02 ~]# tcpdump -i eth0 host192.168.1.11
tcpdump: verbose output suppressed, use -vor -vv for full protocol decode
listening on eth0, link-type EN10MB(Ethernet), capture size 65535 bytes
01:10:31.341271 IP 192.168.1.11 >10.10.1.14: ICMP echo request, id 26629, seq 94, length 64
01:10:31.341298 IP 10.10.1.14 >192.168.1.11: ICMP echo reply, id 26629, seq 94, length 64
01:10:32.341282 IP 192.168.1.11 >10.10.1.14: ICMP echo request, id 26629, seq 95, length 64
01:10:32.341310 IP 10.10.1.14 >192.168.1.11: ICMP echo reply, id 26629, seq 95, length 64
#客户机2ping客户机1
[root@client02 ~]# ping 192.168.1.11
PING 192.168.1.11 (192.168.1.11) 56(84)bytes of data.
64 bytes from 192.168.1.11: icmp_seq=1ttl=62 time=0.752 ms
64 bytes from 192.168.1.11: icmp_seq=2ttl=62 time=0.951 ms
64 bytes from 192.168.1.11: icmp_seq=3ttl=62 time=0.604 ms
64 bytes from 192.168.1.11: icmp_seq=4ttl=62 time=1.02 ms
#路由器1抓取来自客户机2的包
[root@serv02 ~]# tcpdump -i eth0 host10.10.1.14
tcpdump: verbose output suppressed, use -vor -vv for full protocol decode
listening on eth0, link-type EN10MB(Ethernet), capture size 65535 bytes
01:11:36.589348 IP 10.10.1.14 >192.168.1.11: ICMP echo request, id 51205, seq 44, length 64
01:11:36.589971 IP 192.168.1.11 >10.10.1.14: ICMP echo reply, id 51205, seq 44, length 64
01:11:37.590849 IP 10.10.1.14 >192.168.1.11: ICMP echo request, id 51205, seq 45, length 64
01:11:37.591093 IP 192.168.1.11 >10.10.1.14: ICMP echo reply, id 51205, seq 45, length 64
#路由器2抓取来自客户机2的包
[root@serv03 /]# tcpdump -i eth0 host 10.10.1.14
tcpdump: verbose output suppressed, use -vor -vv for full protocol decode
listening on eth0, link-type EN10MB(Ethernet), capture size 65535 bytes
01:11:20.425712 IP 10.10.1.14 >192.168.1.11: ICMP echo request, id 51205, seq 28, length 64
01:11:20.426316 IP 192.168.1.11 >10.10.1.14: ICMP echo reply, id 51205, seq 28, length 64
01:11:21.426282 IP 10.10.1.14 >192.168.1.11: ICMP echo request, id 51205, seq 29, length 64
01:11:21.426769 IP 192.168.1.11 >10.10.1.14: ICMP echo reply, id 51205, seq 29, length 64
01:11:22.426792 IP 10.10.1.14 >192.168.1.11: ICMP echo request, id 51205, seq 30, length 64
01:11:22.427346 IP 192.168.1.11 >10.10.1.14: ICMP echo reply, id 51205, seq 30, length 64
#客户机1抓取来自客户机2的包
[root@client01 ~]# tcpdump -i eth0 host10.10.1.14
tcpdump: verbose output suppressed, use -vor -vv for full protocol decode
listening on eth0, link-type EN10MB(Ethernet), capture size 65535 bytes
01:12:27.549172 IP 10.10.1.14 >192.168.1.11: ICMP echo request, id 51205, seq 95, length 64
01:12:27.549198 IP 192.168.1.11 >10.10.1.14: ICMP echo reply, id 51205, seq 95, length 64
01:12:28.549233 IP 10.10.1.14 >192.168.1.11: ICMP echo request, id 51205, seq 96, length 64
01:12:28.549259 IP 192.168.1.11 >10.10.1.14: ICMP echo reply, id 51205, seq 96, length 64
