4./etc/init.d/httpd restart//重启apache.
5.vi /etc/rc.local写入snort -c /etc/snort/snort.conf&//放在后台运行。
6.利用chkconfig来设置开启启动mysqld ,httpd,snortd//
7.最后把/var/www/html的权限修改一下chmod 755 -R /var/www/html,然后把/var/www/html/setup目录删除或者重命名或者移动保存即可。
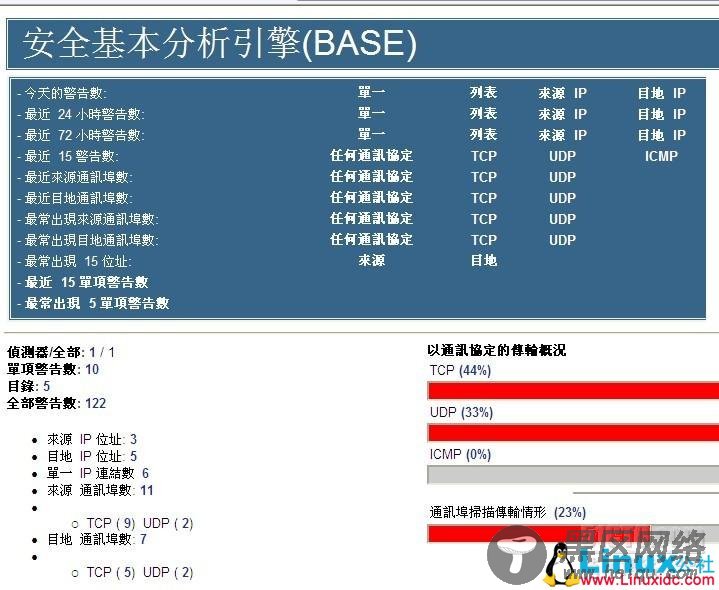
最后测试base
windows平台利用nmap来扫描主机
C:\Documents and Settings\Administrator>nmap -sS 192.168.40.39 -O -v//扫描主机
Starting Nmap 5.51 ( ) at 2012-07-17 16:56 中国标准时间
Initiating ARP Ping Scan at 16:56
Scanning 192.168.40.39 [1 port]
Completed ARP Ping Scan at 16:56, 0.06s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 16:56
Completed Parallel DNS resolution of 1 host. at 16:56, 0.00s elapsed
Initiating SYN Stealth Scan at 16:56
Scanning 192.168.40.39 [1000 ports]
Discovered open port 80/tcp on 192.168.40.39
Discovered open port 22/tcp on 192.168.40.39
Discovered open port 3306/tcp on 192.168.40.39
Completed SYN Stealth Scan at 16:56, 0.08s elapsed (1000 total ports)
Initiating OS detection (try #1) against 192.168.40.39
Nmap scan report for 192.168.40.39
Host is up (0.00s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
MAC Address: 00:0C:29:C8:62:CC (VMware)
Device type: general purpose
Running: Linux 2.6.X
OS details: Linux 2.6.24 - 2.6.35
Uptime guess: 0.003 days (since Tue Jul 17 16:52:28 2012)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=195 (Good luck!)
IP ID Sequence Generation: All zeros
Read data files from: C:\Program Files\Nmap
OS detection performed. Please report any incorrect results at
ubmit/ .
Nmap done: 1 IP address (1 host up) scanned in 2.16 seconds
Raw packets sent: 1020 (45.626KB) | Rcvd: 2030 (82.632KB)
全部警号为98

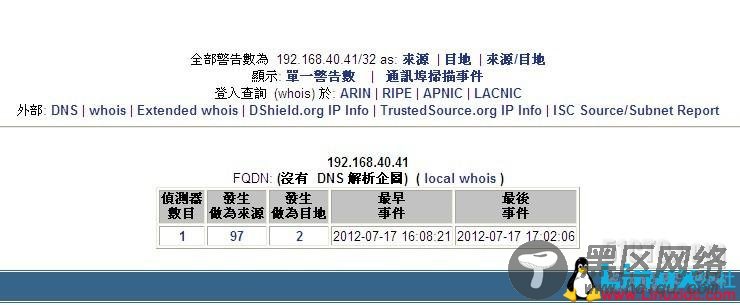
在利用一次nmap扫描工具如下:

全部警告为122了。