一、不安全测试:
1. 安装抓包工具
[root@mail ~]# mount /dev/cdrom /mnt/cdrom
mount: block device /dev/cdrom is write-protected, mounting read-only
[root@mail ~]# cd /mnt/cdrom/Server
[root@mail Server]# ll |grep shark
-r--r--r-- 220 root root 11130359 Jun 11 2009 wireshark-1.0.8-1.el5_3.1.i386.rpm
-r--r--r-- 220 root root 686650 Jun 11 2009 wireshark-gnome-1.0.8-1.el5_3.1.i386.rpm
[root@mail Server]# rpm -ivh wireshark-1.0.8-1.el5_3.1.i386.rpm
warning: wireshark-1.0.8-1.el5_3.1.i386.rpm: Header V3 DSA signature: NOKEY, key ID 37017186
error: Failed dependencies:
libsmi.so.2 is needed by wireshark-1.0.8-1.el5_3.1.i386
[root@mail Server]# ll |grep smi
-r--r--r-- 327 root root 2540456 Jan 18 2008 libsmi-0.4.5-2.el5.i386.rpm
-r--r--r-- 327 root root 21212 Jan 18 2008 libsmi-devel-0.4.5-2.el5.i386.rpm
-r--r--r-- 264 root root 62425 Apr 20 2009 psmisc-22.2-7.i386.rpm
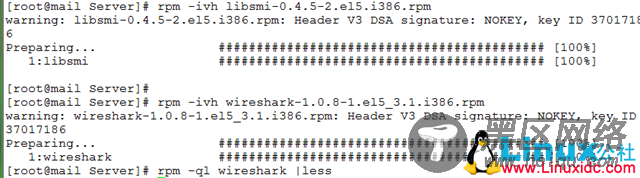
[root@mail Server]# rpm -ql wireshark |less 查看安装路径
2.启动服务
[root@mail ~]# service named start
[root@mail ~]# service dovecot start
[root@mail ~]# service sendmail start
3.启动抓包工具
[root@mail Server]# tshark -ni eth0 -R "tcp.dstport eq 110"
用outlook客户端发送与接收!
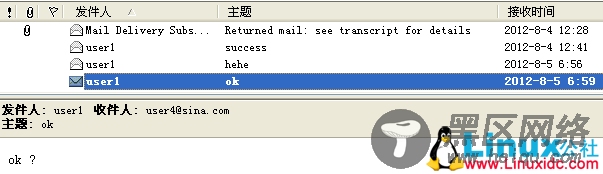
抓到的内容:
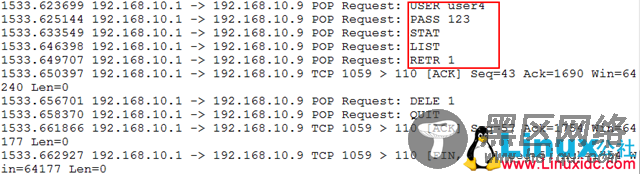
用户名,密码都能看到,这样非常不安全!
二、安全传输:
smtps 465端口,starttls(传输层安全) 25端口
1.数字证书的配置文件:
[root@mail Server]# vim /etc/pki/tls/openssl.cnf
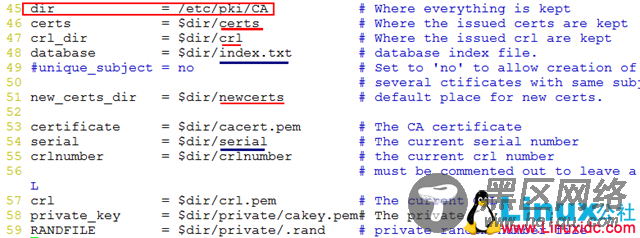
2.生成相应的文件:
[root@mail Server]# cd /etc/pki/CA
[root@mail CA]# mkdir crl certs newcerts
[root@mail CA]# touch index.txt serial
[root@mail CA]# echo "01" >serial
[root@mail CA]# openssl genrsa 1024 > private/cakey.pem
Generating RSA private key, 1024 bit long modulus
....++++++
...................................++++++
e is 65537 (0x10001)
[root@mail CA]# ll private
total 4
-rw-r--r-- 1 root root 887 Aug 5 07:16 cakey.pem
[root@mail CA]# chmod 600 private/*
[root@mail CA]# ll private
total 4
-rw------- 1 root root 887 Aug 5 07:16 cakey.pem
[root@mail CA]# openssl req -new -key private/cakey.pem -x509 -days 3650 -out cacert.pem
Country Name (2 letter code) [GB]: 出现这个!
3.CA的认证机构:
[root@mail CA]# vim /etc/pki/tls/openssl.cnf
:88,90s/match/optional
[root@mail CA]# openssl req -new -key private/cakey.pem -x509 -days 3650 -out cacert.pem
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [CN]:
State or Province Name (full name) [He Nan]:
Locality Name (eg, city) [Zheng zhou]:
Organization Name (eg, company) [My Company Ltd]:tec center
Organizational Unit Name (eg, section) []:diver agent
Common Name (eg, your name or your server's hostname) []:mail.com
4.为发送服务器申请一个证:
[root@mail CA]# mkdir -pv /etc/mail/certs
mkdir: created directory `/etc/mail/certs'
[root@mail CA]# cd /etc/mail/certs/
[root@mail certs]# openssl genrsa 1024 >sendmail.key 钥匙
Generating RSA private key, 1024 bit long modulus
............++++++
............................++++++
e is 65537 (0x10001)
[root@mail certs]# openssl req -new -key sendmail.key -out sendmail.csr 请求文件
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [CN]:
State or Province Name (full name) [He Nan]:
Locality Name (eg, city) [Zheng zhou]:
Organization Name (eg, company) [My Company Ltd]:163
Organizational Unit Name (eg, section) []:tecnology
Common Name (eg, your name or your server's hostname) []:mail.163.com
[root@mail certs]# openssl ca -in sendmail.csr -out sendmail.cert //证书
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Aug 4 23:46:58 2012 GMT
Not After : Aug 4 23:46:58 2013 GMT
Subject:
countryName = CN
stateOrProvinceName = He Nan
organizationName = 163
organizationalUnitName = tecnology
commonName = mail.163.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
93:33:1C:69:DC:7E:20:B9:C4:F7:37:D5:F8:15:3F:48:A2:C4:36:C4
X509v3 Authority Key Identifier:
keyid:FE:69:9D:8E:DE:9A:A4:AA:6D:F5:A6:EF:17:DD:AA:CD:D0:59:7E:1E
Certificate is to be certified until Aug 4 23:46:58 2013 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
已经产生证书,此时,请求文件可以删除了!
