这个jenkins-slave是一个剧本主要来启动这个slave.jar,那么这个还需
要一个docker情况,自己这个pod就是以docker container启动的,那么这个pod也就可以做数据卷挂载了,因为这个pod是在每个node上去启动的,每个node上都有docker,那么直接就可以把每个node上的docker挂载到容器中就可以了,所以这就用到了一个docker in docker,这个容器内里又有了一个docker的情况,所以我们需要写数据卷将它挂载进来,尚有kubectl这个定名,一般主要来查察pod的一些状态,并且利用这个呼吁来完成k8s的各类百般的操纵,可是需要它这个呼吁,只需要它毗连k8s的认证信息,因为k8s有它的鉴权
此刻将这个镜像打包成镜像推送到镜像客栈中
构建镜像的时候可以直接写harbor的地点加镜像的名称,这样直接可以push,否则构建完还得打个tag
[root@k8s-master jenkins-slave]# docker build . -t 192.168.30.27/library/jenkins-slave:jdk-1.8 [root@k8s-master jenkins-slave]# docker push 192.168.30.27/library/jenkins-slave查察客栈已经将镜像推送乐成
此刻就可以去测试能不能动态的去建设jenkins-slave,需要将pipeline这个剧本能去挪用适才我们设置的k8s的插件
jenkins官方地点给出了相关的pipeline挪用k8s的插件的用法
github地点:https://plugins.jenkins.io/kubernetes
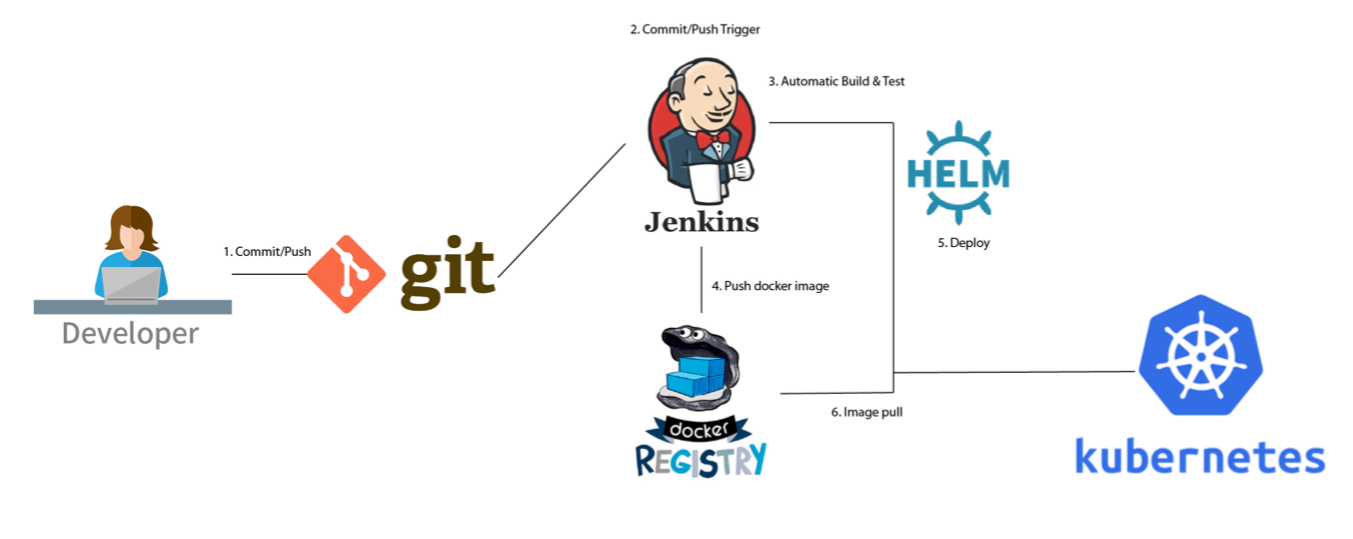
七、基于kubernetes构建jenkins ci系统
此刻去动态的在pipeline去引用并建设一个slave的镜像,利用pipeline在k8s去运行这个pod,然后将这个pod宣布我们的任务,适才我们是先安装的插件,以对jenkins可以实现slave的署理,可以正常去交互,又建造了我们的slave的镜像,将java所需的设置也都封装在这个slave内里这样的话,我们就可以回收这个slave来完成下发的任务了,而master只作为一个打点节点给他们下发任务到slave上
这就是我们的pipeline,此刻今朝是可以利用我们这个slave这个镜像来宣布任务
安装pipeline插件
pipeline { agent { kubernetes { label 'jenkins-slave' yaml """ apiVersion: v1 kind: Pod metadata: name: jenkins-slave spec: containers: - name: jnlp image: "192.168.30.27/library/jenkins-slave:jdk-1.8" """ } } stages { stage('Build') { steps { echo "hello" } } stage('test') { steps { echo "hello" } } stage('deploy') { steps { echo "hello" } } } }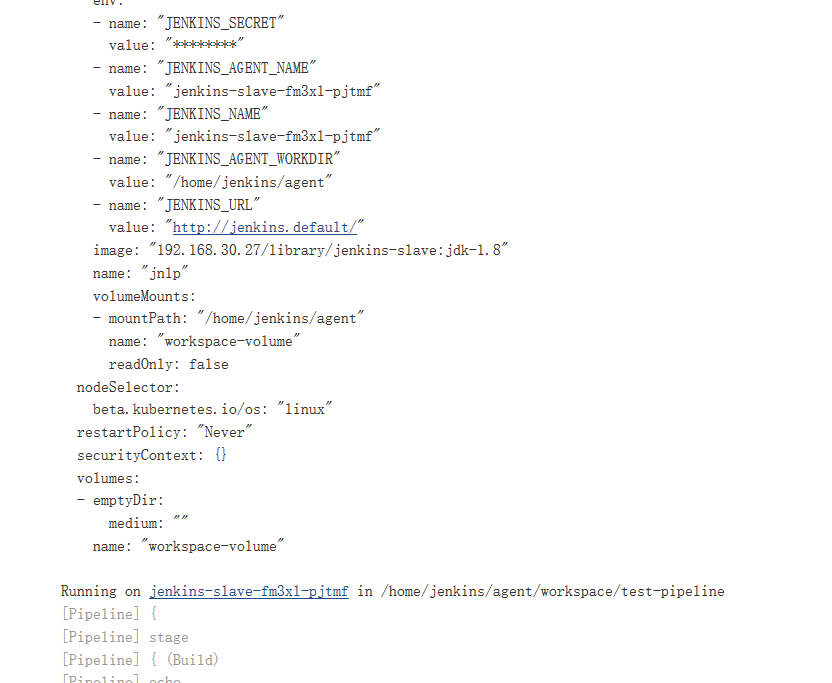
此刻可以在jenkins中动态的去建设pod,只有有下发任务的时候才去建设pod,而jenkins-master只认真任务调治,slave来做任务处理惩罚来节减资源,当任务完成之后,这个slave-pod也会自动的销毁
[root@k8s-master1 ~]# kubectl get pod
NAME READY STATUS RESTARTS AGE
jenkins-7d5fbd857d-6tgdj 1/1 Running 0 23m
jenkins-slave-gdtqz-p17b1 1/1 Running 0 40s
八、pipeline集成helm宣布spring cloud微处事
此刻编写这个pipeline脚原来实现自动化宣布微处事 #!/usr/bin/env groovy // 所需插件: Git Parameter/Git/Pipeline/Config File Provider/kubernetes/Extended Choice Parameter // 民众 def registry = "192.168.30.27" // 项目 def project = "microservice" def git_url = "http://192.168.30.28/root/ms.git" def gateway_domain_name = "gateway.zhaocheng.com" def portal_domain_name = "portal.zhaochengr.com" // 认证 def image_pull_secret = "registry-pull-secret" def harbor_registry_auth = "e5402e52-7dd0-4daf-8d21-c4aa6e47736b" def git_auth = "a65680b4-0bf7-418f-a77e-f20778f9e737" // ConfigFileProvider ID def k8s_auth = "7ee65e53-a559-4c52-8b88-c968a637051e" pipeline { agent { kubernetes { label "jenkins-slave" yaml """ kind: Pod metadata: name: jenkins-slave spec: containers: - name: jnlp image: "${registry}/library/jenkins-slave-jdk:1.8" imagePullPolicy: Always volumeMounts: - name: docker-cmd mountPath: /usr/bin/docker - name: docker-sock mountPath: /var/run/docker.sock - name: maven-cache mountPath: /root/.m2 volumes: - name: docker-cmd hostPath: path: /usr/bin/docker - name: docker-sock hostPath: path: /var/run/docker.sock - name: maven-cache hostPath: path: /tmp/m2 """ } } parameters { gitParameter branch: '', branchFilter: '.*', defaultValue: '', description: '选择宣布的分支', name: 'Branch', quickFilterEnabled: false, selectedValue: 'NONE', sortMode: 'NONE', tagFilter: '*', type: 'PT_BRANCH' extendedChoice defaultValue: 'none', description: '选择宣布的微处事', \ multiSelectDelimiter: ',', name: 'Service', type: 'PT_CHECKBOX', \ value: 'gateway-service:9999,portal-service:8080,product-service:8010,order-service:8020,stock-service:8030' choice (choices: ['ms', 'demo'], description: '陈设模板', name: 'Template') choice (choices: ['1', '3', '5', '7'], description: '副本数', name: 'ReplicaCount') choice (choices: ['ms'], description: '定名空间', name: 'Namespace') } stages { stage('拉代替码'){ steps { checkout([$class: 'GitSCM', branches: [[name: "${params.Branch}"]], doGenerateSubmoduleConfigurations: false, extensions: [], submoduleCfg: [], userRemoteConfigs: [[credentialsId: "${git_auth}", url: "${git_url}"]] ]) } } stage('代码编译') { // 编译指定处事 steps { sh """ mvn clean package -Dmaven.test.skip=true """ } } stage('构建镜像') { steps { withCredentials([usernamePassword(credentialsId: "${harbor_registry_auth}", passwordVariable: 'password', usernameVariable: 'username')]) { sh """ docker login -u ${username} -p '${password}' ${registry} for service in \$(echo ${Service} |sed 's/,/ /g'); do service_name=\${service%:*} image_name=${registry}/${project}/\${service_name}:${BUILD_NUMBER} cd \${service_name} if ls |grep biz &>/dev/null; then cd \${service_name}-biz fi docker build -t \${image_name} . docker push \${image_name} cd ${WORKSPACE} done """ configFileProvider([configFile(fileId: "${k8s_auth}", targetLocation: "admin.kubeconfig")]){ sh """ # 添加镜像拉取认证 kubectl create secret docker-registry ${image_pull_secret} --docker-username=${username} --docker-password=${password} --docker-server=${registry} -n ${Namespace} --kubeconfig admin.kubeconfig |true # 添加私有chart客栈 helm repo add --username ${username} --password ${password} myrepo ${registry}/chartrepo/${project} """ } } } } stage('Helm陈设到K8S') { steps { sh """ common_args="-n ${Namespace} --kubeconfig admin.kubeconfig" for service in \$(echo ${Service} |sed 's/,/ /g'); do service_name=\${service%:*} service_port=\${service#*:} image=${registry}/${project}/\${service_name} tag=${BUILD_NUMBER} helm_args="\${service_name} --set image.repository=\${image} --set image.tag=\${tag} --set replicaCount=${replicaCount} --set imagePullSecrets[0].name=${image_pull_secret} --set service.targetPort=\${service_port} myrepo/${Template}" # 判定是否为新陈设 if helm history \${service_name} \${common_args} &>/dev/null;then action=upgrade else action=install fi # 针对处事启用ingress if [ \${service_name} == "gateway-service" ]; then helm \${action} \${helm_args} \ --set ingress.enabled=true \ --set ingress.host=${gateway_domain_name} \ \${common_args} elif [ \${service_name} == "portal-service" ]; then helm \${action} \${helm_args} \ --set ingress.enabled=true \ --set ingress.host=${portal_domain_name} \ \${common_args} else helm \${action} \${helm_args} \${common_args} fi done # 查察Pod状态 sleep 10 kubectl get pods \${common_args} """ } } } }
