POST :8001/upstreams/u-http1/targets --data target='192.168.43.94:5000'
POST :8001/upstreams/u-http1/targets --data target='192.168.43.94:5001'
4.修改http1 service的指向,让其指向u-htttp1这个upstream
PATCH :8001/services/server1 --data host='u-http1'
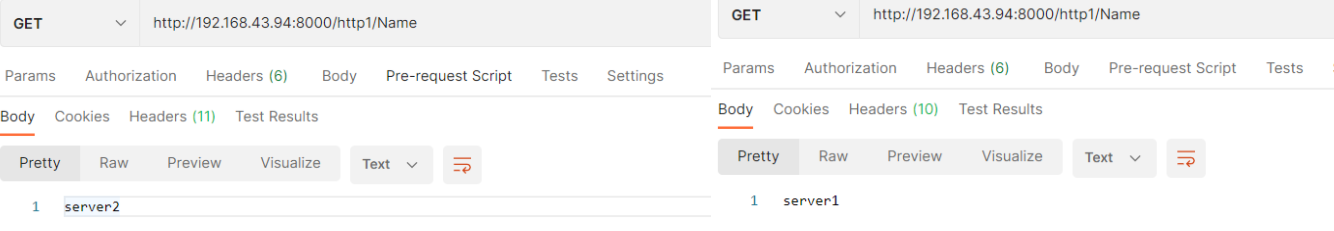
5.测试,调用以下api
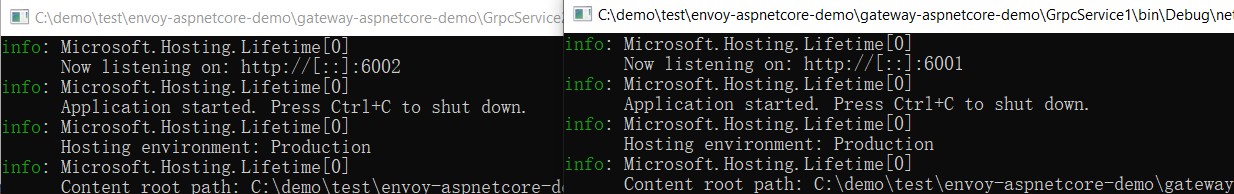
1.启动GrpcService1与GrpcService2
2.通过admin api在Kong中创建upstreams,也可使用可视化界面Konga创建
POST :8001/upstreams --data name=u-gserver1
3.为u-gserver1创建target,指向GrpcService1与GrpcService2
POST :8001/upstreams/u-gserver1/targets --data target='192.168.43.94:6001'
POST :8001/upstreams/u-gserver1/targets --data target='192.168.43.94:6002'
4.修改gserver1 service的指向,让其指向u-gserver1这个upstream
PATCH :8001/services/gserver1 --data host=‘u-gserver1'
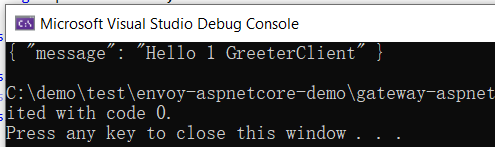
5.测试,运行GrpcClient

1.给server1开启jwt插件
POST :8001/services/server1/plugins -d “name=jwt ” –d “config.key_claim_name=client_id”
2.创建consumer
POST localhost:8001/consumers -d "username=c-server1"
3.获取ids4证书公钥与私钥
openssl安装https://slproweb.com/products/Win32OpenSSL.html
openssl pkcs12 -in chester.pfx -nocerts -nodes -out private_pc.key 从密钥对中提取私钥(头部格式:-----BEGIN RSA PUBLIC KEY-----) openssl rsa -in private_pc.key -out private.pem 从密钥对提取公钥(头部格式:-----BEGIN PUBLIC KEY-----) openssl rsa -in private_pc.key -pubout -out public.key
4.为C-server1创建凭证
POST localhost:8001/consumers/c-server1/jwt -d "algorithm=RS256" -d "key=big_cat" -d "secret=xxxxxx" -d "rsa_public_key=xxxxxxxxx“
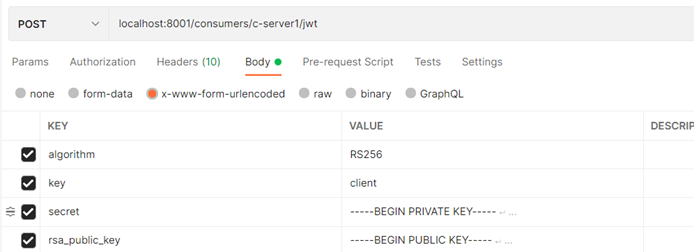
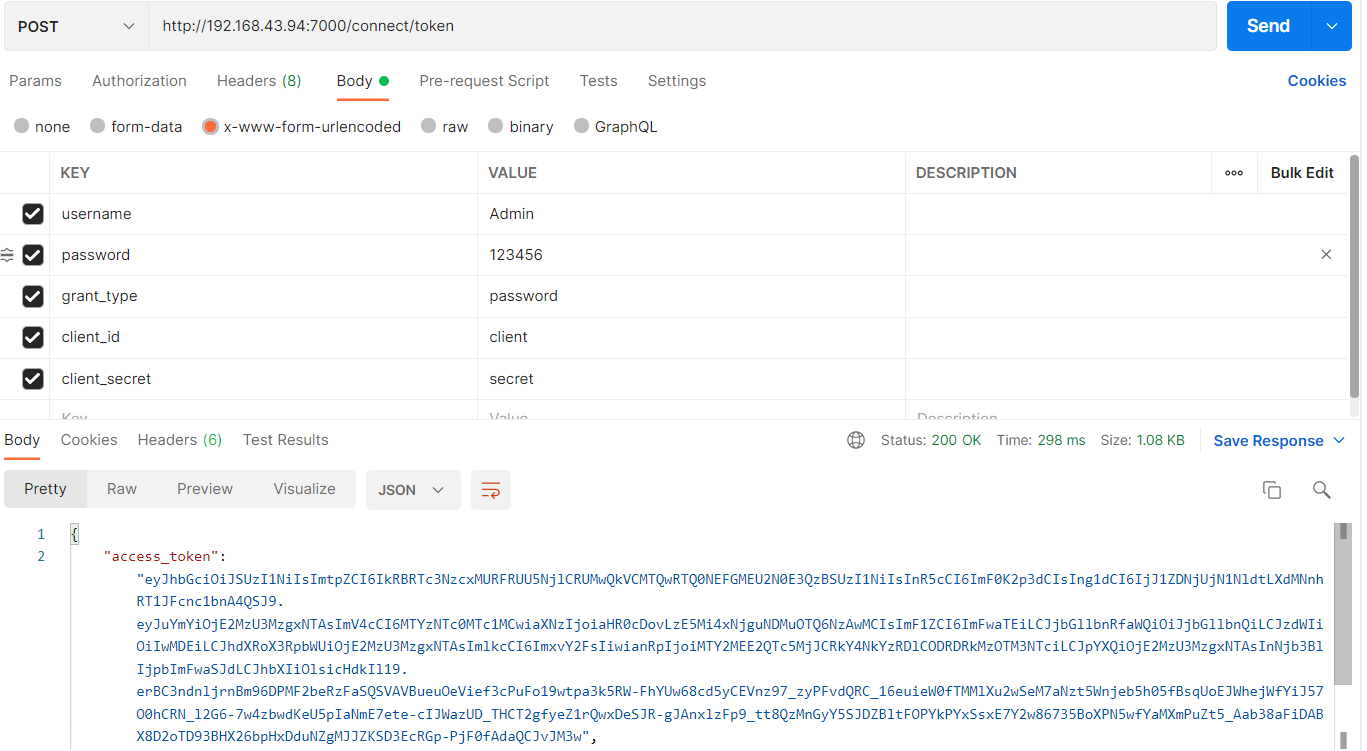
5.启动id4test获取jwttoken
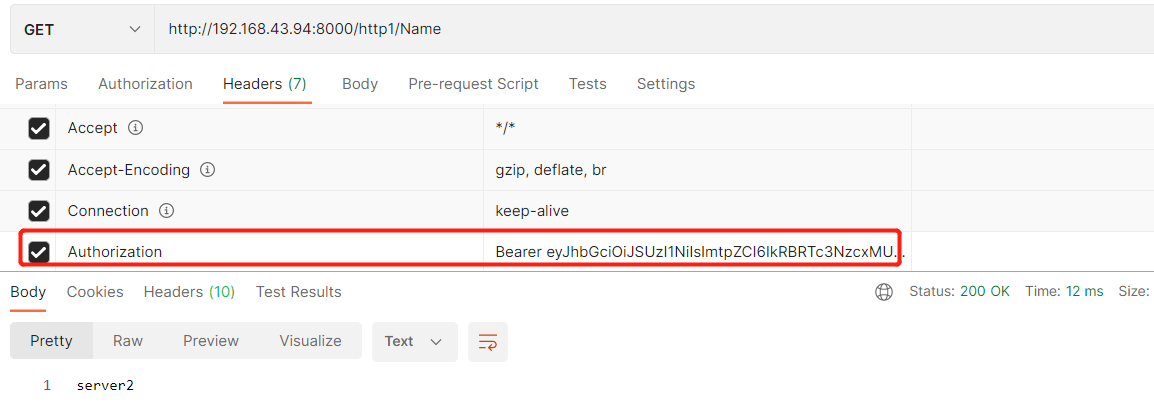
6.调用api验证token
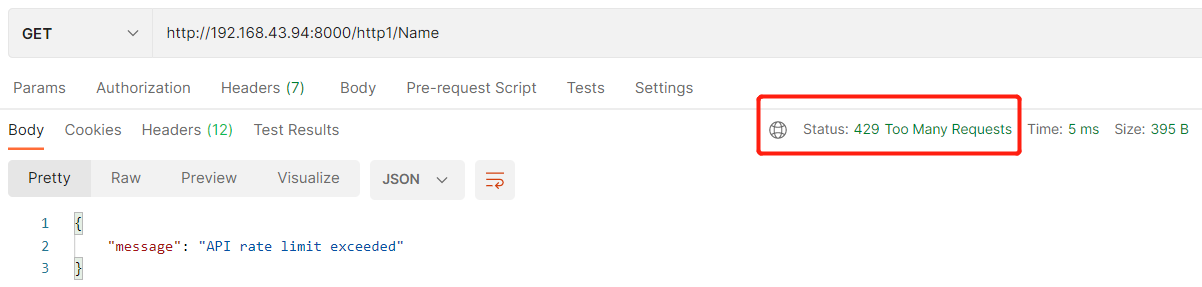
POST <admin-hostname>:8001/plugins --data name=rate-limiting --data config.minute=5 --data config.policy=redis --data redis_host=192.168.43.102 --data limit_by=ip –data redis_password=123456
多次调用触发则触发限流
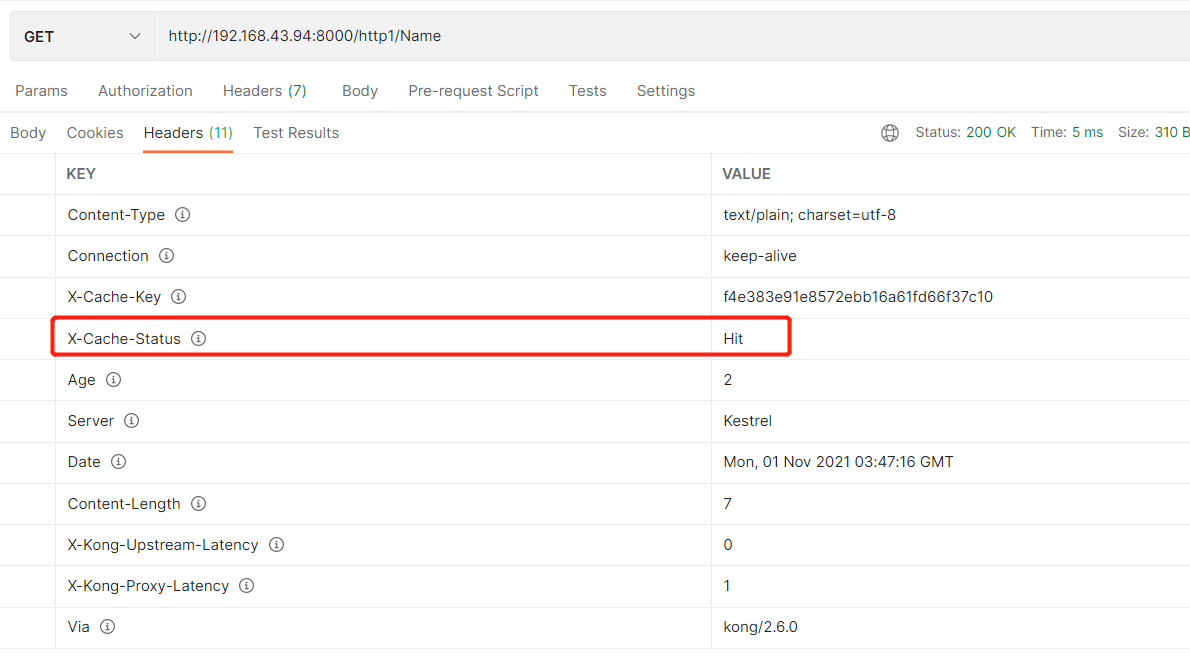
POST :8001/plugins --data name=proxy-cache --data config.content_type="text/plain; charset=utf-8" --data config.cache_ttl=30 --data config.strategy=memory
多次调用X-Cache-Status=Hit则命中缓存成功
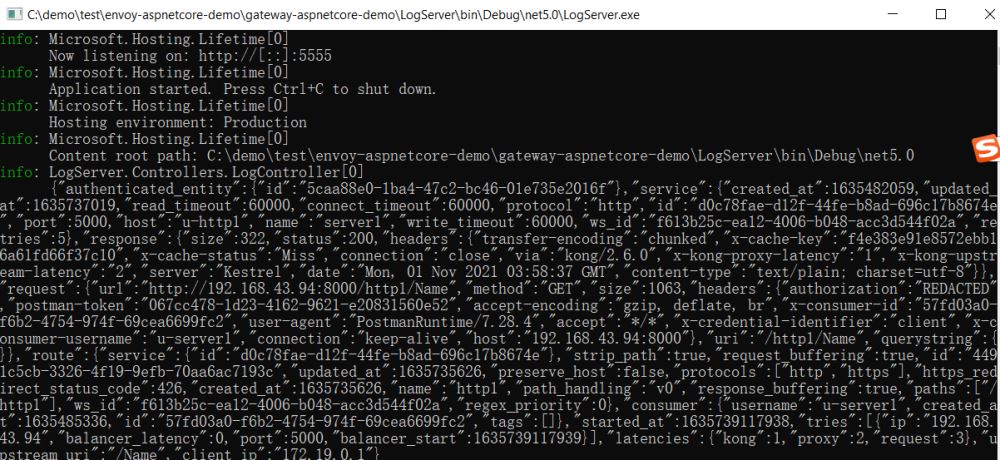
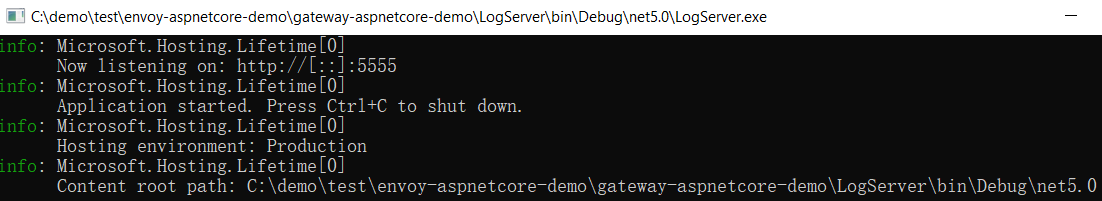
启动LogServer
开启日志插件
POST :8001/services/server1/plugins --data "name=http-log" --data "config.http_endpoint=http://192.168.43.94:5555/Log" --data "config.method=POST"
请求:8000/http1/Name,查看LogServer输出