提示:官方参考yaml:https://raw.githubusercontent.com/kubernetes/dashboard/v2.2.0/aio/deploy/recommended.yaml。
修改yaml [root@master01 dashboard]# vi recommended.yaml …… kind: Service apiVersion: v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard spec: type: NodePort #新增 ports: - port: 443 targetPort: 8443 nodePort: 30001 #新增 selector: k8s-app: kubernetes-dashboard --- …… #如下全部注释 #apiVersion: v1 #kind: Secret #metadata: # labels: # k8s-app: kubernetes-dashboard # name: kubernetes-dashboard-certs # namespace: kubernetes-dashboard #type: Opaque …… kind: Deployment …… replicas: 3 #适当调整为3副本 …… spec: containers: - name: kubernetes-dashboard image: kubernetesui/dashboard:v2.1.0 imagePullPolicy: IfNotPresent #修改镜像下载策略 ports: - containerPort: 8443 protocol: TCP args: - --auto-generate-certificates - --namespace=kubernetes-dashboard - --tls-key-file=tls.key - --tls-cert-file=tls.crt - --token-ttl=3600 #追加如上args …… nodeSelector: "kubernetes.io/os": linux "dashboard": "yes" #部署在master节点 …… kind: Service apiVersion: v1 metadata: labels: k8s-app: dashboard-metrics-scraper name: dashboard-metrics-scraper namespace: kubernetes-dashboard spec: type: NodePort #新增 ports: - port: 8000 targetPort: 8000 nodePort: 30000 #新增 selector: k8s-app: dashboard-metrics-scraper …… replicas: 3 #适当调整为3副本 …… nodeSelector: "beta.kubernetes.io/os": linux "dashboard": "yes" #部署在master节点 …… 正式部署 [root@master01 dashboard]# kubectl apply -f recommended.yaml [root@master01 dashboard]# kubectl get deployment kubernetes-dashboard -n kubernetes-dashboard [root@master01 dashboard]# kubectl get services -n kubernetes-dashboard [root@master01 dashboard]# kubectl get pods -o wide -n kubernetes-dashboard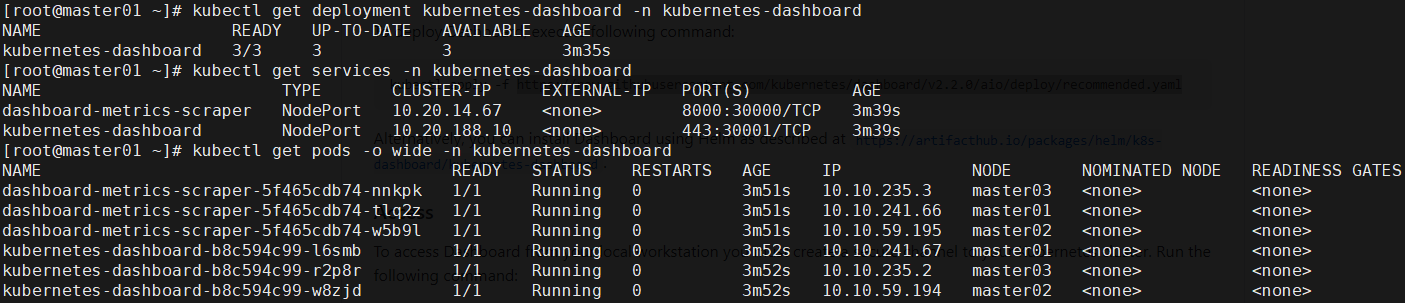
提示:master01 NodePort 30001/TCP映射到 dashboard pod 443 端口。
创建管理员账户提示:dashboard v2版本默认没有创建具有管理员权限的账户,可如下操作创建。
[root@master01 dashboard]# vi dashboard-admin.yaml --- apiVersion: v1 kind: ServiceAccount metadata: name: admin-user namespace: kubernetes-dashboard --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: admin-user roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: cluster-admin subjects: - kind: ServiceAccount name: admin-user namespace: kubernetes-dashboard[root@master01 dashboard]# kubectl apply -f dashboard-admin.yaml
ingress暴露dashboard 创建ingress tls [root@master01 ~]# cd /root/dashboard/certs [root@master01 certs]# kubectl -n kubernetes-dashboard create secret tls kubernetes-dashboard-tls --cert=tls.crt --key=tls.key [root@master01 certs]# kubectl -n kubernetes-dashboard describe secrets kubernetes-dashboard-tls
将dashboard.odocker.com证书导入浏览器,并设置为信任,导入操作略。
创建kubeconfig文件使用token相对复杂,可将token添加至kubeconfig文件中,使用KubeConfig文件访问dashboard。
[root@master01 dashboard]# ADMIN_SECRET=$(kubectl -n kubernetes-dashboard get secret | grep admin-user | awk '{print $1}') [root@master01 dashboard]# DASHBOARD_LOGIN_TOKEN=$(kubectl describe secret -n kubernetes-dashboard ${ADMIN_SECRET} | grep -E '^token' | awk '{print $2}') [root@master01 dashboard]# kubectl config set-cluster kubernetes \ --certificate-authority=http://www.likecs.com/etc/kubernetes/pki/ca.crt \ --embed-certs=true \ --server=172.16.10.254:16443 \ --kubeconfig=ucloud-ngkeconk8s-dashboard-admin.kubeconfig # 设置集群参数 [root@master01 dashboard]# kubectl config set-credentials dashboard_user \ --token=${DASHBOARD_LOGIN_TOKEN} \ --kubeconfig=ucloud-ngkeconk8s-dashboard-admin.kubeconfig # 设置客户端认证参数,使用上面创建的 Token [root@master01 dashboard]# kubectl config set-context default \ --cluster=kubernetes \ --user=dashboard_user \ --kubeconfig=ucloud-ngkeconk8s-dashboard-admin.kubeconfig # 设置上下文参数 [root@master01 dashboard]# kubectl config use-context default --kubeconfig=ucloud-ngkeconk8s-dashboard-admin.kubeconfig # 设置默认上下文将ucloud-ngkeconk8s-dashboard-admin.kubeconfig文件导入,以便于浏览器使用该文件登录。
测试访问dashboard本实验采用ingress所暴露的域名:https://dashboard.odocker.com 方式访问。使用ucloud-ngkeconk8s-dashboard-admin.kubeconfig文件访问。


